4.6.4. Targets
Targets offer quite an extensive selection of different types, so that a very precise distinction must be made here between what is to be achieved with the respective type.
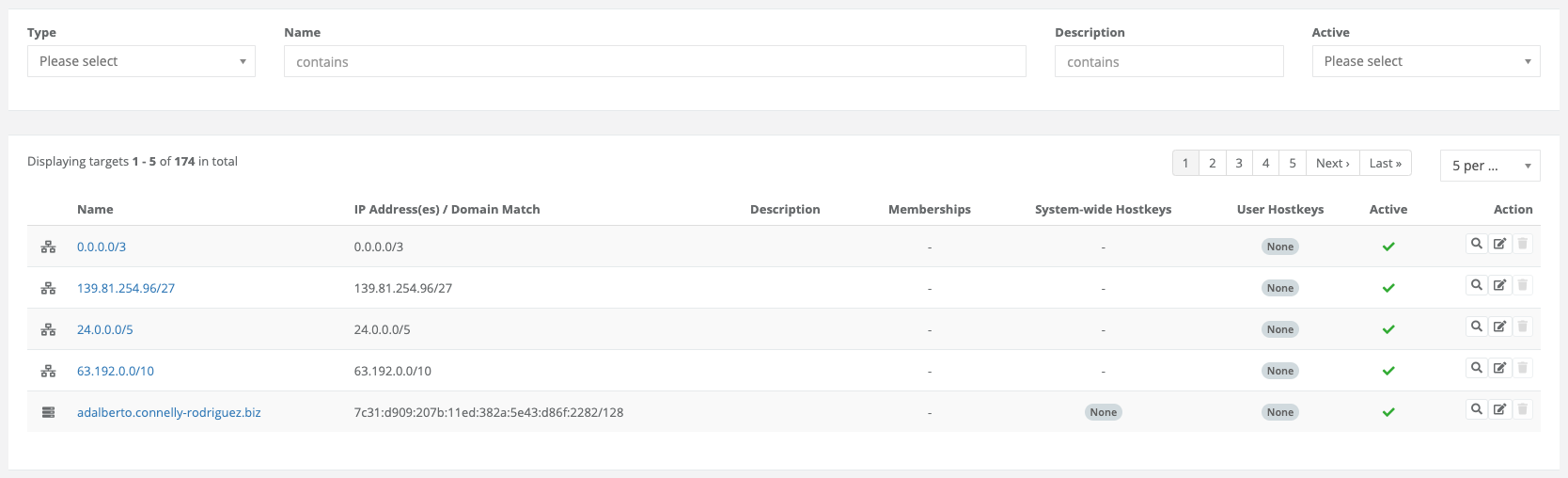
4.6.4.1. Static Targets
Static targets are targets that identify themselves uniquely via their IP address. You could also say that they are the safest objects compared to the other types, because they have to be configured statically in the network.
For static targets, one or more IP addresses are defined and one or more public hostkeys are stored. If multiple IP addresses are stored, they must still represent the same host with the same hostkey. It is therefore advisable to store multiple IP addresses only if they belong to the same host.
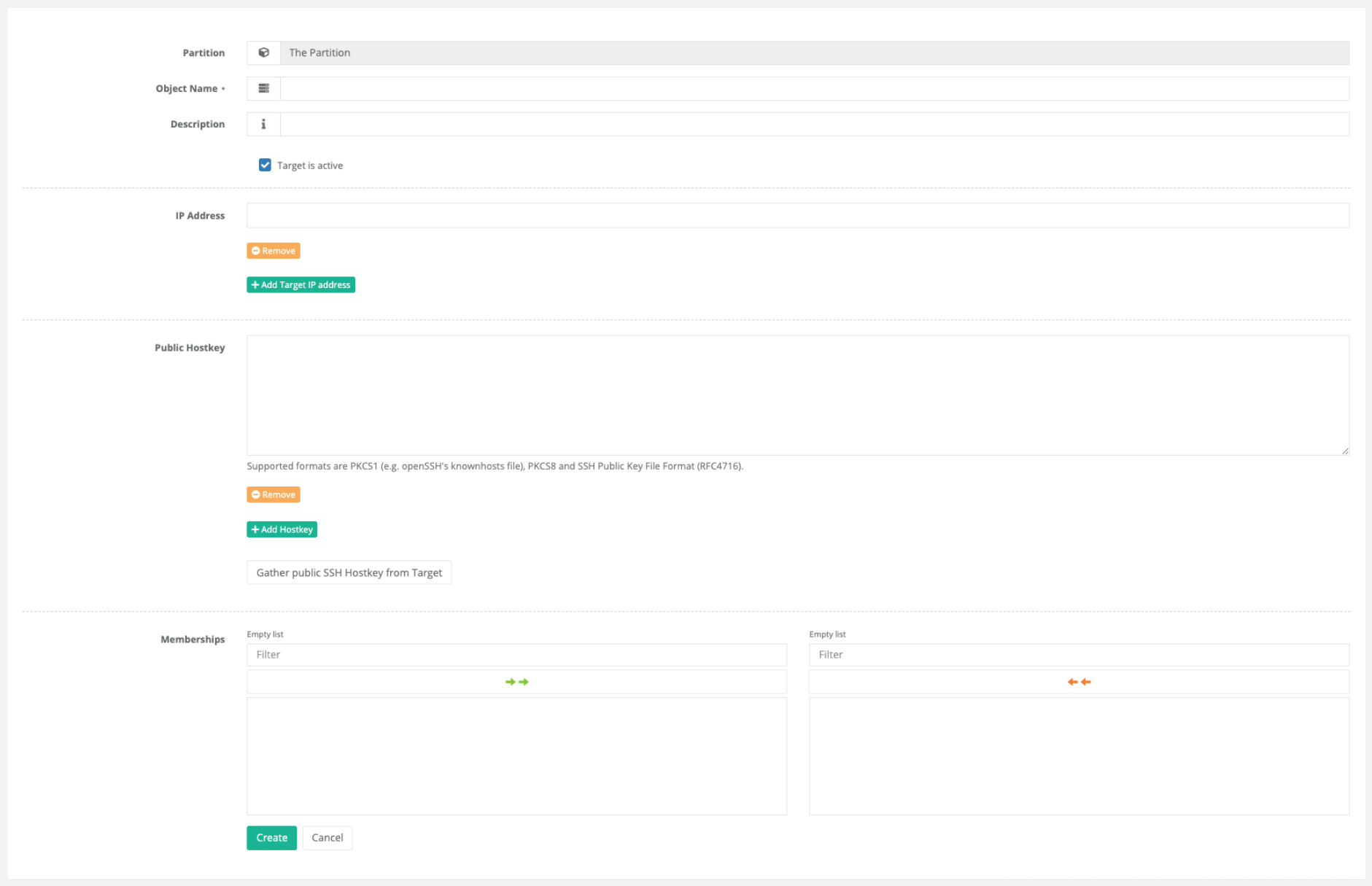
To save the manual import of a hostkey, the button Gather public SSH Hostkey from Target can be pressed, whereupon
suSSHi Chef will instruct a suSSHi Gateway to request the hostkey.

Of course, it must also be ensured in this case that no man-in-the-middle attack has taken place at the time of the query and that you can be sure of the imported key. The fingerprint and type of the retrieved key are also displayed.
4.6.4.2. Network Target
Network targets can be used to authorize an entire network as a target or, as we will see later, to be used in a deny rule. For example, access to entire networks from certain sources and/or user (groups) can be prevented in a single rule.
If a network target is authorized, a public hostkey for this network cannot be stored in advance, of course, since in most cases it will probably be a network with several individual hosts. In this case, it is only possible to learn and store the public hostkeys for each user individually - similar to the normal behavior of an SSH client when a user accesses a target. We will come back to this later.
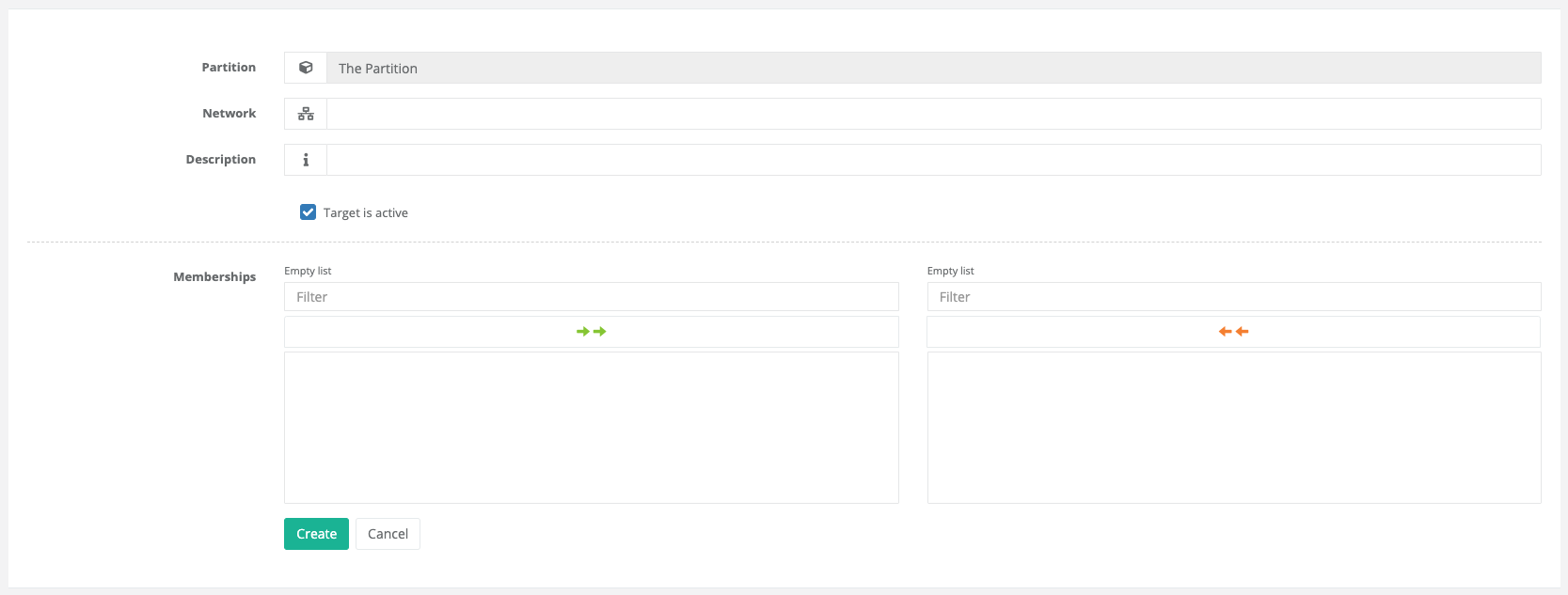
Please create the object with an IPv4 or IPv6 network in CIDR notation. And as always, you can add this single object to a group.
4.6.4.3. Dynamic Target
Dynamic Targets are quite comparable to the static target, with the difference that here not the IP address(es), but the FQDN of the target is of central importance.
For dynamic targets, the suSSHi Gateway performs a DNS lookup at the time of a new connection and connects to the corresponding IP address it obtained via DNS.
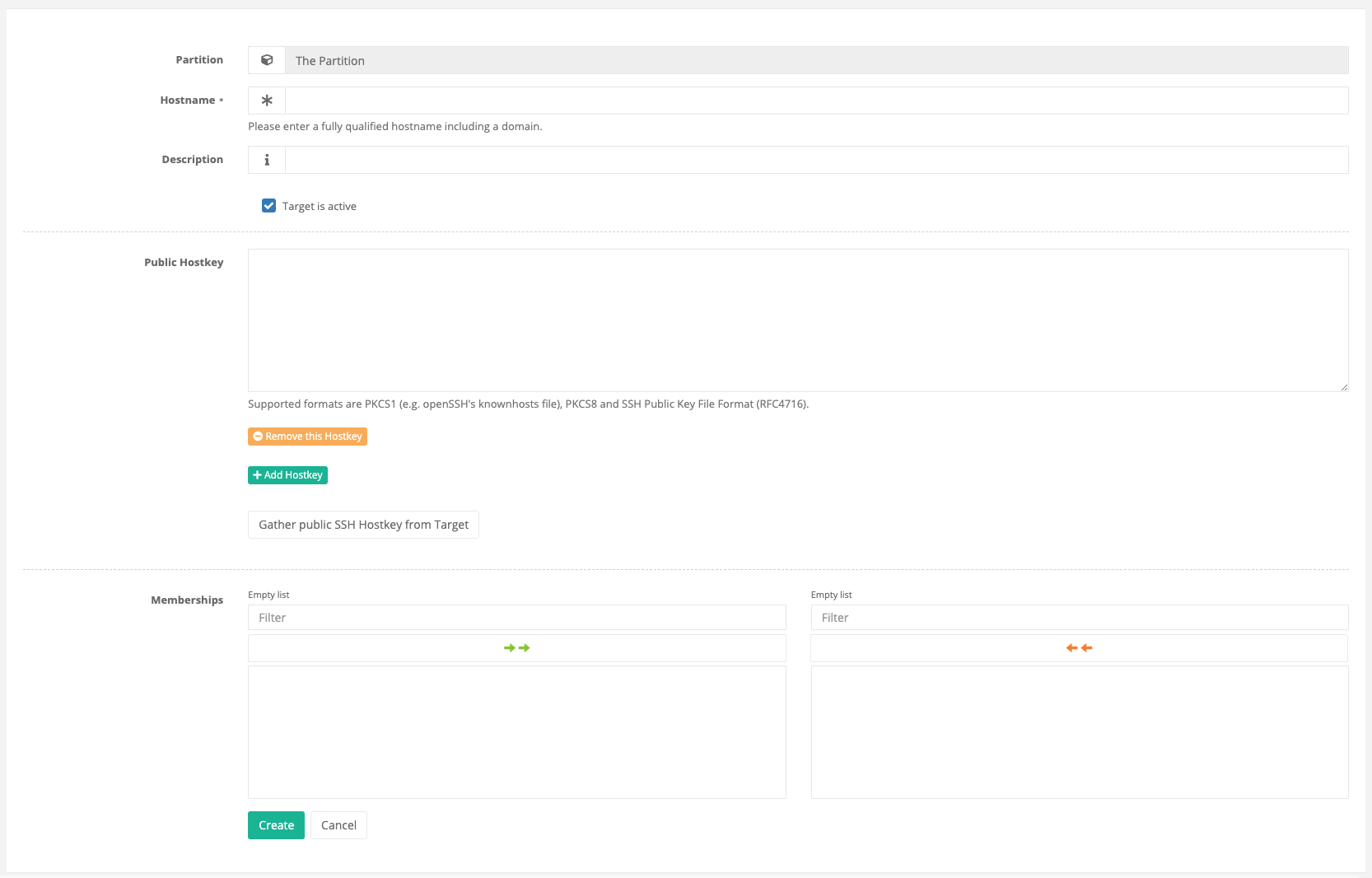
Likewise, click Gather public SSH Hostkey from Target to import the hostkey manually.
Warning
Theoretically, this type of target is more susceptible to man-in-the-middle attacks, since DNS manipulation may not address the expected target machine. Therefore, verifying the public hostkey at the time of import is even more important here.
4.6.4.4. Domain Target
Domain targets, in turn, are very comparable to network targets, especially with regard to hostkeys. However, they differ in that the target IP address does not have to fit into a specific network range, but the target’s FQDN must lie within a DNS domain.
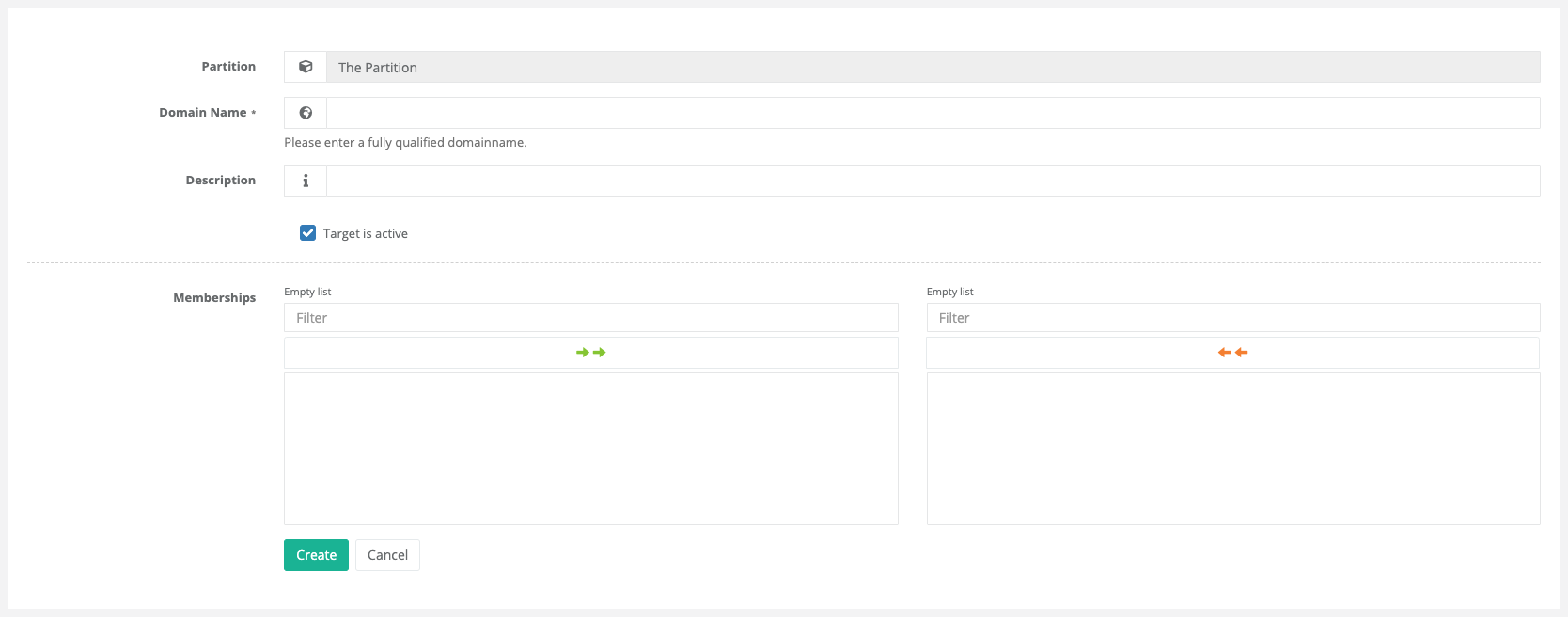
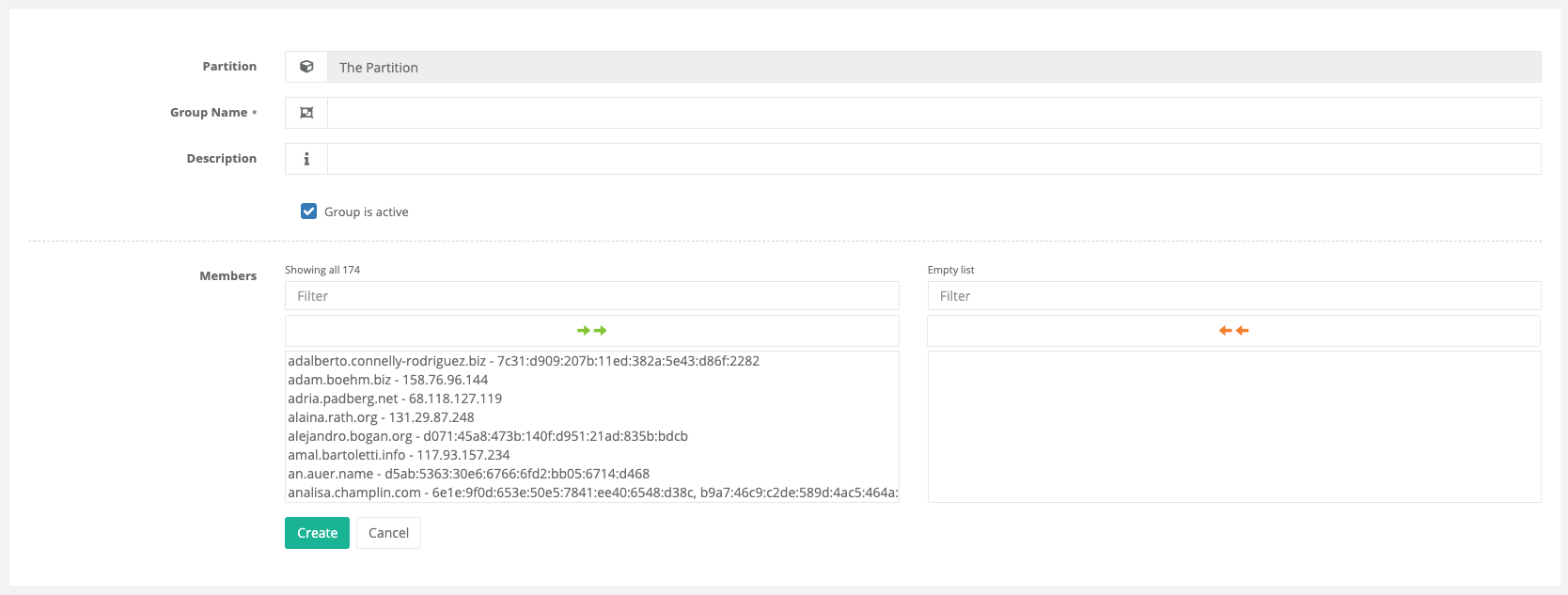
4.6.4.5. Group Objects
Group objects are used to combine individual objects so that this group can later be used in an access rule. Group objects cannot be nested in other group objects.
4.6.4.6. Scan Network
This menu item does not represent a separate target type, but allows scanning a network area for active hosts with an SSH service and their public hostkeys.
This point is very handy because it generates a list of the found hosts together with their public hostkey fingerprint and the FQDNs obtained from the DNS reverse lookup as a result of the scan.
In this list, each individual object can then be deselected if required, before all the objects found can be created with
a single click.
It is even possible to immediately add the objects to an existing or newly created group.
The created target objects are always of type Static Target.

Please specify either an IPv4 network with a maximum prefix mask of 20 bits (/20) or an IPv6 network with a maximum prefix mask of 116 bits (/116). This is a safety measure to avoid that the scan tries to detect a too large range and the scan runs too long.
If an IP address within a range is unreachable, the gateway tries for up to 3 seconds, which can mean a total scan time of up to 13 minutes for 254 individual IP addresses.
After the scan is completed, you will be redirected to the results overview.
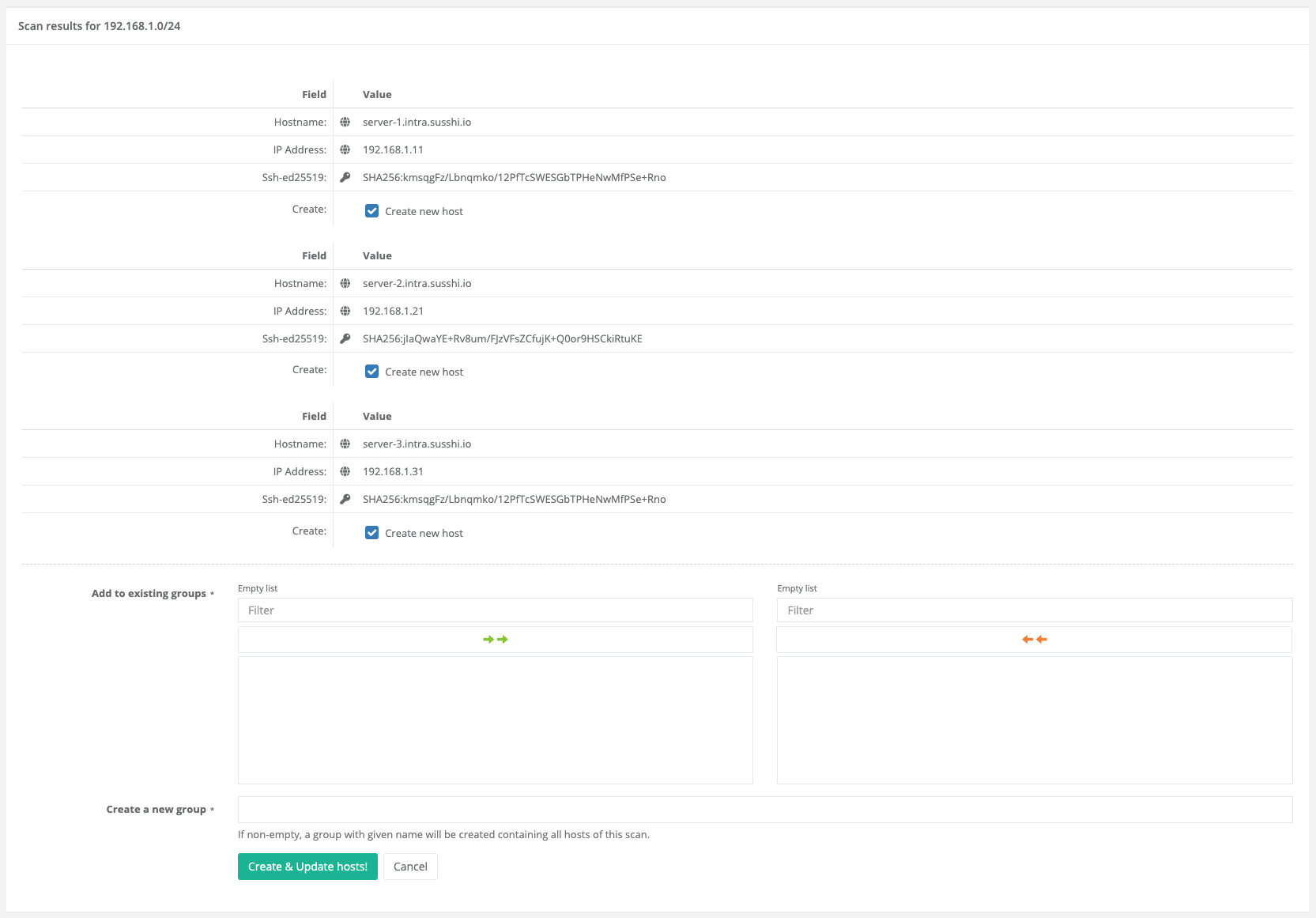
To add/create/update the scanned targets to suSSHi Chef, click Create & Updated hosts!.
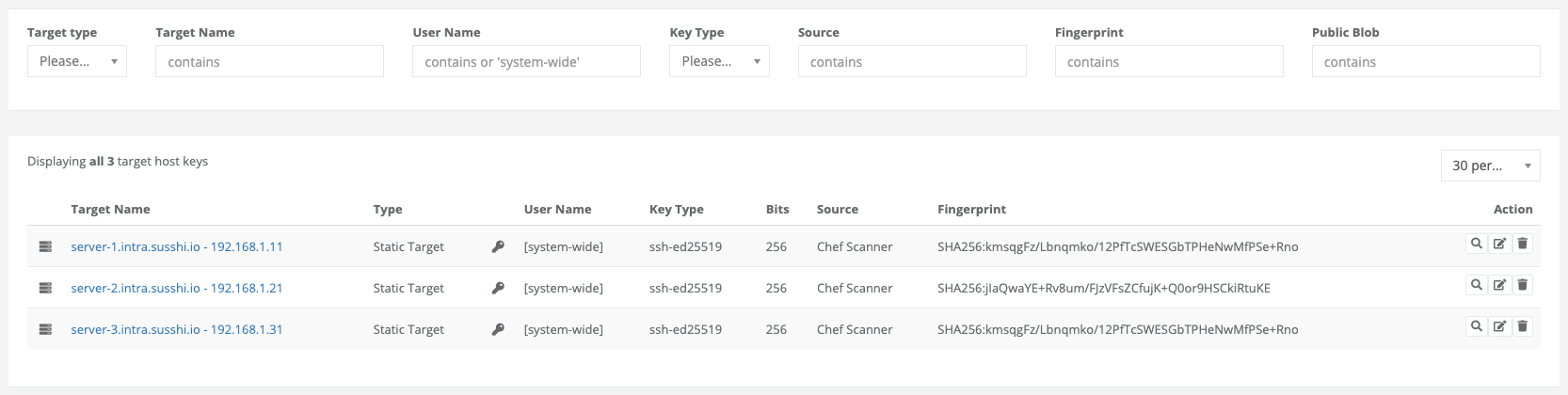
4.6.4.7. Target Hostkeys
Hostkeys may change or targets may become obsolete. This menu allows you to view, update and delete collected hostkeys.