4.5. Access Rules
Access rules are the central point of contact when it comes to deciding what a user who establishes a connection via a suSSHi Gateway is ultimately allowed to do. The access rules decide from which source IP a gateway user is allowed to access which target, with which target user and with which profile. The rights are derived from profiles that control what type of access (interactive, non-interactive, file copy, etc.), whether port forwarding, etc. is allowed and how the session should be recorded.
Let’s take a look at an example rule:
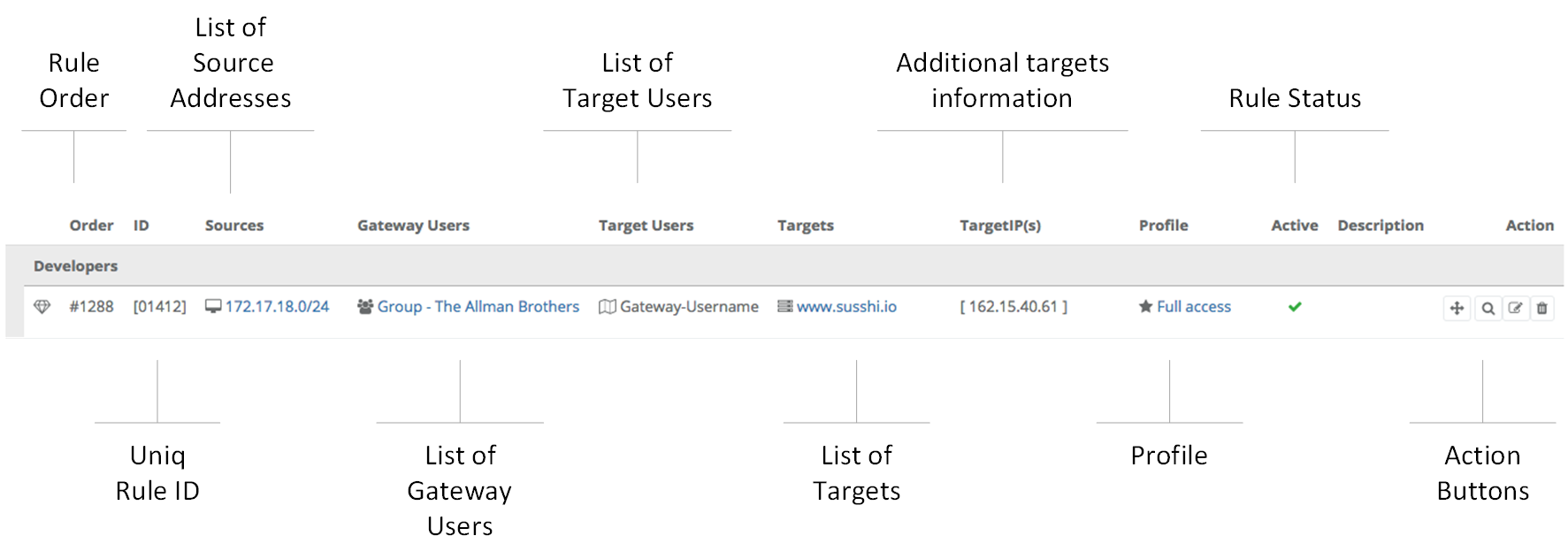
As you can see, the access rules provide the overall picture of a set of rules that define access to your systems. We will now look at the individual elements before returning to the access rules at the end for a closer look at how to deal with them.
4.5.1. Access Rule Objects
The various access rule objects are later used in the actual access rules and are explained in more detail here:
4.5.2. Access Policies
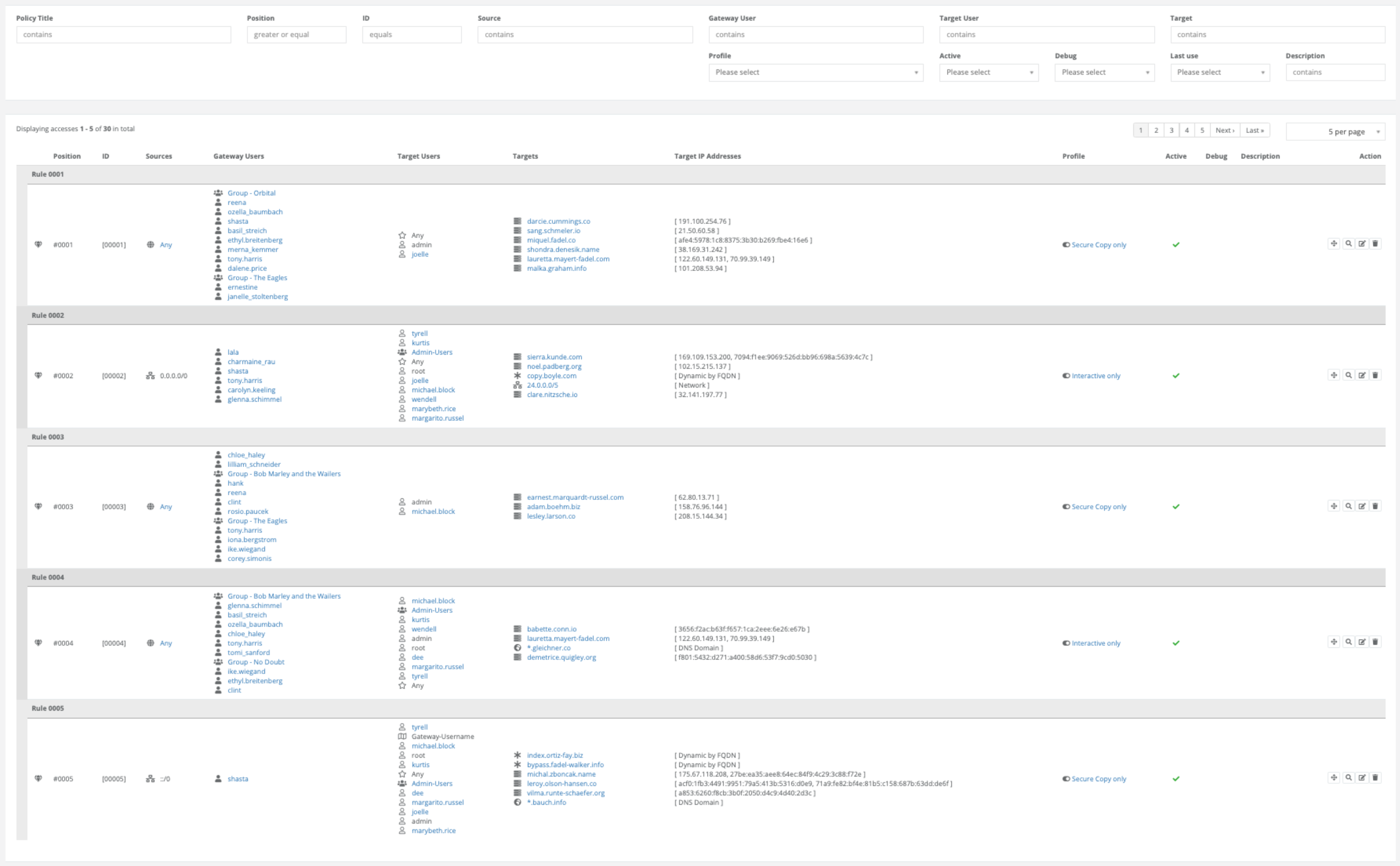
Now that we have learned about the individual elements, we can look at how they are used in a ruleset.
The ruleset is structured to be searched from top to bottom based on the input parameters of a new session consisting of
source, gateway user, target user and target, and the first hit is evaluated as the best hit.
The selected profile of this match will then be applied to the connection.
If, for example, the name resolution of the gateway (or proxies) results in several possible target IP addresses, the best (first) match in the entire ruleset is assumed for each individual IP and reported back to the gateway. If a connection is established, the profile of the target IP address to which the gateway was able to establish a connection is used.
4.5.2.1. Adding a new Rule
By default, a new rule is created at the end of the ruleset. If the rule is to be specifically inserted at a different position, this position can be selected via a drop-down.
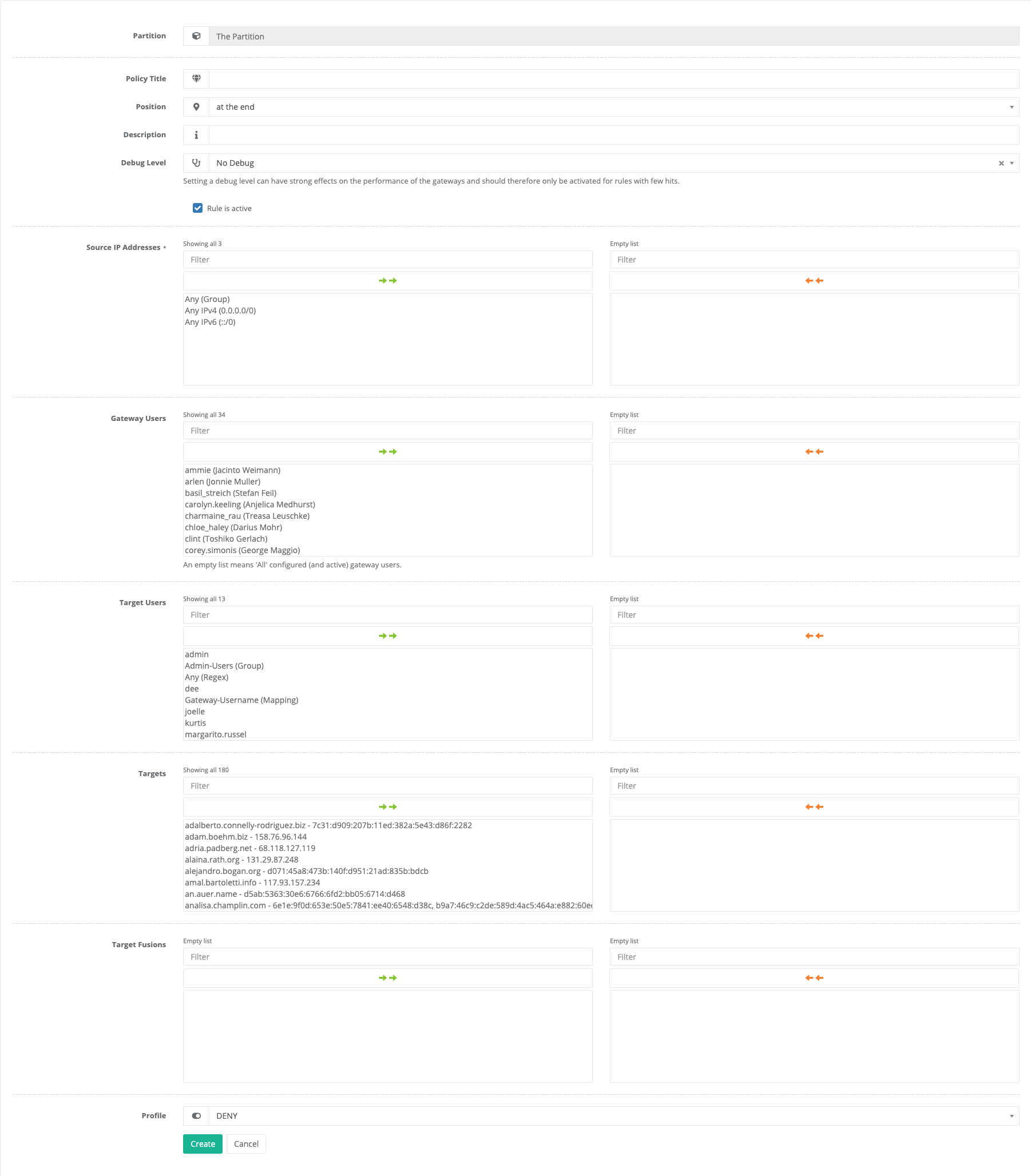
Please enter all required data in the corresponding fields. An empty list of gateway users means “All” configured (and active) gateway users.
4.5.2.2. Moving a Rule
There are two ways to move a rule within the ruleset:
Drag-and-drop
Simply grab the relevant rule with the mouse in the left area and move it up or down. The move takes place directly and the ruleset is reloaded in its new order.
“Move policy rule” Action
Click the
Move policy ruleAction and select the new position from the drop-down menu.“Edit Access” Action
When editing a rule, you can use the
Positiondrop-down menu to choose another position within the ruleset.
4.5.2.3. Removing a Rule
By pressing the trash can button, a rule can be easily removed after confirming this step.